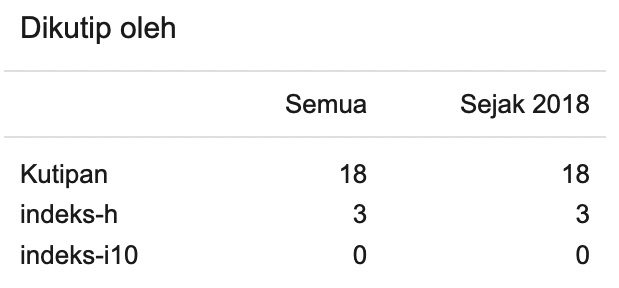
Peningkatan Kesadaran Keamanan Informasi Siswa SMK Telkom Purwokerto Melalui Pelatihan Footprinting dan Reconnaissance
Abstract
The community service activity aims to delve into the concept of footprinting and reconnaissance in cybersecurity focusing on students at SMK Telkom Purwokerto. Guided by lecturers and students, the activity aims to enhance participants' understanding of vital early information analysis and gathering techniques in the realm of cybersecurity. Implementation methods include online learning and direct practical sessions in the classroom, enabling participants to implement these concepts. The training benefits encompass an improved understanding of system security threats, the development of technical analysis skills, and the ability to implement better protective measures. The results demonstrate active participation and an enhanced understanding of the importance of footprinting and reconnaissance in managing information security risks among the participants. There was a 90% increase in awareness after the participants underwent the training, indicating a positive impact of this activity on students' comprehension of information security. Therefore, this activity not only supports the tridharma of higher education but also strengthens the relationship between the Telkom Purwokerto Institute of Technology and the community in enhancing local cybersecurity.
References
Alwi, E. I., & Ilmawan, L. B. (2021). Analisis Keamanan Sistem Informasi Akademik (SIAKAD) Universitas XYZ Menggunakan Metode Vulnerability Assessment. INFORMAL: Informatics Journal, 6(3). https://doi.org/10.19184/isj.v6i3.27053
Dinis, B., & Serrão, C. (2014). Using PTES and open-source tools as a way to conduct external footprinting security assessments for intelligence gathering. Journal of Internet Technology and Secured Transaction, 3(3), 271–279. https://doi.org/10.20533/jitst.2046.3723.2014.0035
Edgar, T. W., & Manz, D. O. (2017). Research Methods for Cyber Security. In Research Methods for Cyber Security. https://doi.org/10.1016/s1353-4858(18)30053-9
Flores, F., Paredes, R., & Meza, F. (2016). Procedures for mitigating Cybersecurity risk in a Chilean Government Ministry. IEEE Latin America Transactions, 14(6), 2947–2950. https://doi.org/10.1109/TLA.2016.7555280
Ghonge, M. M., Pramanik, S., Mangrulkar, R., & Le, D. N. (2021). Cyber Security and Digital Forensics. In Cyber Security and Digital Forensics. https://doi.org/10.1002/9781119795667
Lenjani, A., Dyke, S. J., Bilionis, I., Yeum, C. M., Kamiya, K., Choi, J., Liu, X., & Chowdhury, A. G. (2020). Towards fully automated post-event data collection and analysis: Pre-event and post-event information fusion. Engineering Structures, 208. https://doi.org/10.1016/j.engstruct.2019.109884
Muni, A., Sudeska, E., Crismondari, C., Jalil, M., & Bayu Rianto. (2023). OPTIMALISASI IT DALAM ERA LITERISASI DIGITAL. SWARNA: Jurnal Pengabdian Kepada Masyarakat, 2(1). https://doi.org/10.55681/swarna.v2i1.263
Soesanto, E., Romadhon, A., Dwi Mardika, B., & Fahmi Setiawan, M. (2023). Analisis dan Peningkatan Keamanan Cyber: Studi Kasus Ancaman dan Solusi dalam Lingkungan Digital Untuk Mengamankan Objek Vital dan File. SAMMAJIVA : Jurnal Penelitian Bisnisdan Manajemen, 1(2).
Styugin, M. (2019). Protection from reconnaissance for establishing information security systems. Information Security Journal, 28(1–2), 46–54. https://doi.org/10.1080/19393555.2019.1630528
Sutejo, S., Prasetijo, A. B., & Agushyban, F. (2021). The Role of Information System for Risk Management in Hospital: A Narrative Review. Jurnal Aisyah : Jurnal Ilmu Kesehatan, 6(3). https://doi.org/10.30604/jika.v6i3.1014
Thoyyibah, T. (2018). Evaluasi Manajemen Keamanan Informasi Menggunakan Indeks Keamanan Informasi (KAMI) berdasarkan ISO 27001:2013 Pada Pusat Informasi dan Pangkalan Data Perguruan Tinggi X. Jurnal CoreIT: Jurnal Hasil Penelitian Ilmu Komputer Dan Teknologi Informasi, 4(2), 72. https://doi.org/10.24014/coreit.v4i2.6292
Copyright (c) 2024 IJCOSIN: Indonesian Journal of Community Service and Innovation

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.